Traceable Tackles Deeper Data Protection Use Cases with Latest API Security Platform Update


Today, we are excited to announce enhanced data protection capabilities in our API Security platform component, API Protection! This update focuses on providing proactive protection against deeper and broader API abuse attempts that lead to fraud, and the compromising of sensitive data.
APIs are the interconnectivity pipe through which data flows between applications, and to and from users, including threat actors. As the amount of sensitive data which flows through APIs increases, it is imperative that security teams get a better understanding of the volumes of traffic leaving their apps.
From fake account creation to account takeovers, to sensitive data exfiltration, to API Fraud, and the abuse of APIs – the security industry needs a new approach to ensure APIs don’t become a constant attack vector for data breaches.
API Abuse and Fraud are Now the Biggest Data Security Issues Across Multiple Industries
Gartner predicted that API abuse will be the most common type of attack seen in 2022. And here we are.
So, what problems exactly do APIs face? And what can data security leaders do about it?
The challenge of API security is gaining more traction as API data breaches become more prevalent. Here are some examples of API security incidents that made the headlines, just last year.
- Security researchers found that all of the 30 health care apps they studied were at risk of API attacks. They also learned that the apps exposed 23 million users to potential threats.
- An API tool used by Experian, exposed the credit scores of almost every person in the United States. The tool enabled someone to perform a credit check through the credit bureau using only public information.
- Another API problem involved Peloton. A researcher found that they could make unauthenticated requests to the company’s API for user account data. That weakness enabled anyone to access the information of other bike owners.
What is API Abuse?
First, let’s take a step back and clearly define API Abuse. API abuse refers to the act of mishandling APIs. Typically, this mishandling is intentional and malicious, but there are situations of accidental misuse. Some examples include gaining unsanctioned access, and modifying functionalities so that APIs can be used for raiding or overburdening servers. In many cases, it’s performed with the help of malicious bots, or even manually inserting malicious code.
These activities often lead to sensitive data loss, price changes to store items, and gaining fraudulent access to bank accounts and financial information. In many cases, these attack types lead to significant operational downtime.
It’s important to note that not all API abuse attacks leverage vulnerabilities. APIs can be exploited using their own design. Just like in the cases of Venmo and Coinbase, the APIs were functioning exactly how they were supposed to. Therefore, simply performing an API design analysis would not have given any meaningful information as to the security (or lack thereof) of those APIs.
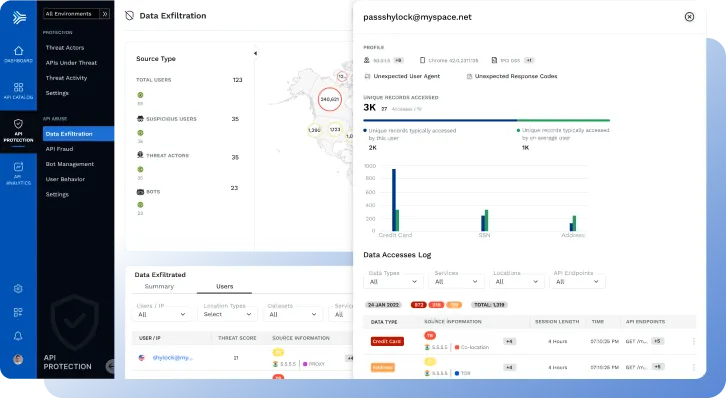
Traceable's API Protection Capabilities: Protection Against Abuse, Fraud, and Sensitive Data Exfiltration
These enhanced data security capabilities address the fundamental business and financial risks, and operational downtime often associated with API data breaches.
In terms of features and capabilities, this release includes the following:
- Track volumes of sensitive data traversing between APIs over time
- Users can establish a baseline of API sequences and user behavior to detect fraudulent activities.
- Categorize users’ accessing data through APIs (e.g., partners, data owners, threat actors, and more)
- Create customizable data sets for enhanced data protection and compliance capabilities
- Enhanced detection accuracy is also available with various sensors including geolocation, Tor, Botnet, proxy, and malicious bots (e.g., scraper, spam, botnet).
- Additional capabilities include the ability to correlate with increases in account takeover or excessive login attempts.
- Detection of fraud for materially significant data (e.g., gift cards, loyalty points, free credits, and much more).
“Traceable’s technology packs multiple security solutions into a single integrated solution, and with their new data exfiltration detection allows businesses of all types to know if their data is at risk and be able to stop that risk.”
- Tim Davis, Director of Risk at Chime
Traceable Continues to Build on its API Security Platform's Existing Capabilities, which include:
- API Discovery and Security Posture: Traceable automatically discovers and identifies all external API endpoints and internal APIs in a data-rich catalog for complete visibility and identification of organizations’ API estate and sprawl. Shadow and orphaned APIs are identified, and users are notified of any API changes. It maps app topologies and data flows, including connectivity between edge APIs, internal services, and data stores.
- Protection against Sensitive Data Exfiltration: Security teams can immediately detect where hackers gain access to sensitive data by exploiting software bugs or CVEs. Understand the flow of transactions through the application - from the edge to the data store and back - to quickly respond and mitigate risk. Organizations can respond to API threats with API bot mitigation - preventing runtime exploitation tracking users and threat actors.
- Threat Hunting: Traceable provides a rich set of security and application flow analytics, which can be used by SOC teams or security analysts. Teams can hunt for hidden IOCs and breaches, track and trace activities of suspicious users, run post-mortem analyses of security incidents, spot malicious users, speed incident response, and lower mean time to resolution.
- Flexible deployment options:
- Fully out-of-band collection via network log analysis of AWS, Google Cloud Platform (GCP), and Azure clouds - specifically for highly regulated industries.
- Collection by instrumentation within your API gateway, proxies, or service mesh.
- In-app data collection through instrumentation by language-specific agents or via socket filtering.
- Agent or agentless deployment depending on business requirements.
Start Your API Security Journey Today
With the API threat landscape increasing in scope and sophistication, we are thrilled to continue delivering API security solutions to address your growing challenges. We encourage you to request a demo of API Protection to get the full experience of how it can address your API Security needs.
Multiple Options to Get Started
Depending on your role and the needs at your organization, we offer multiple options to get started with Traceable AI:
- If you’re a CISO or DevSecOps security leader and want to evaluate your API security risks, try our API Security Posture Assessment.
- To start your journey, sign up for our Free Tier and learn all about your APIs — internal, external, third-party, and even the shadow or rogue APIs you may not even be aware of.
- If you want to compare different API security solutions in the market, check out our API Security Tools comparison guide.
- You can also view a demo or book a meeting to learn more and ask your questions on how Traceable can meet your API security requirements.
The Inside Trace
Subscribe for expert insights on application security.
.avif)



