The Uber API Authorization Vulnerability


What Happened
In September 2019, a critical bug was discovered on Uber API, which allows merchants, service providers and others to offer ride-sharing services to customers. Uber had exposed a vulnerable application programming interface (API) endpoint that allowed attackers to steal valuable data, including personally identifiable information (PII) records and authentication tokens of riders and drivers. The leaked authentication token could be used to perform a full account takeover.
Luckily for the company, the vulnerability was discovered before harm could be done. But the case is an example of where traditional security systems can fail to find potential threats because they lack the business context for the application’s logic. Let’s take a closer look at what happened and the implications.
Technical Details
When a new Uber driver joins the platform through a referral link, their browser communicates with the API host “bonjour.uber.com”. The registration process triggers an API call to the API endpoint of:
POST /marketplace/\_rpc?rpc=getConsentScreenDetails

The API receives the “userUuid” parameter from the client and returns details about the user. This information is used to populate the consent screen on the client-side:
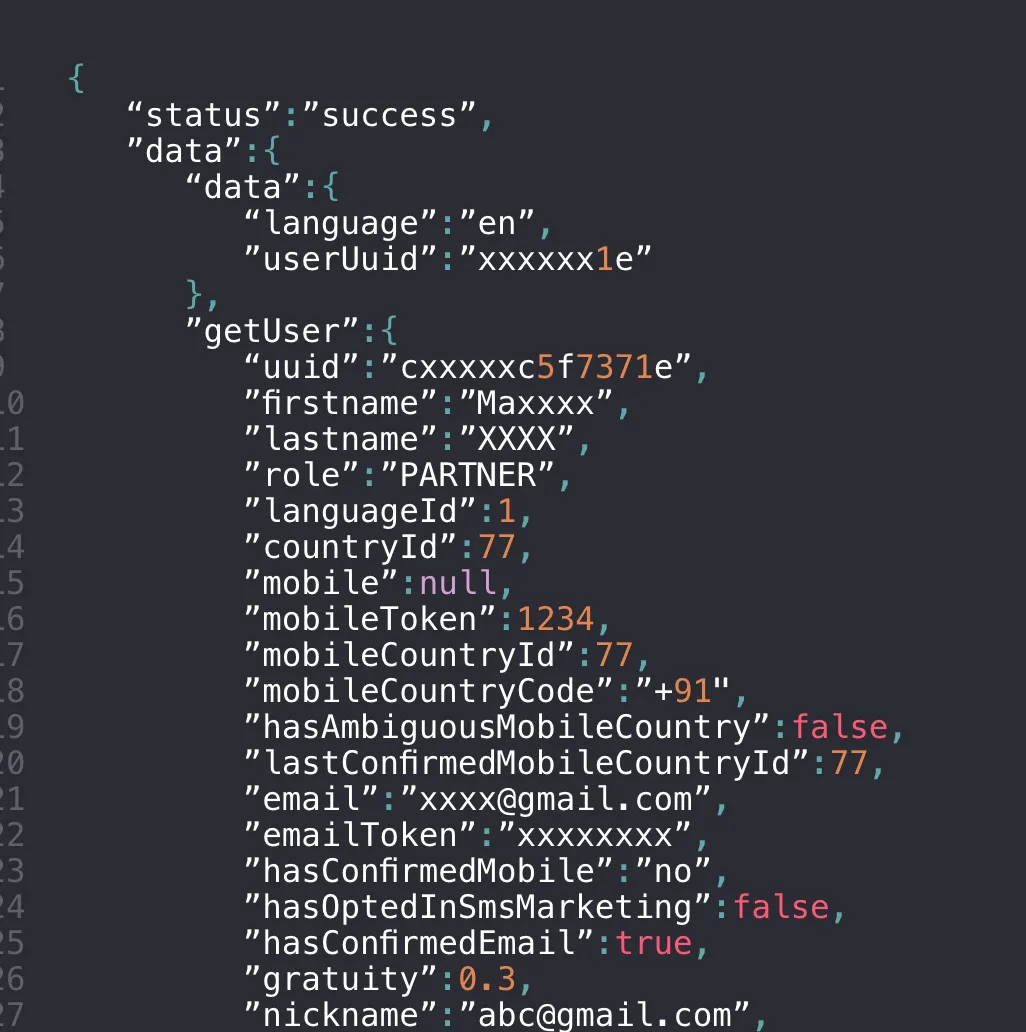
As part of a legit flow, the user should send only his own user ID.
The API endpoint is susceptible to two types of API vulnerabilities:
- BOLA (Broken Object Level Authorization). Because the program didn’t validate that the client who sent the request had access to the user represented by the user ID parameter, the client could access data of other users by changing the user ID.
- Excessive Data Exposure. The API response contains a large JSON object with all the user’s details. The API returned this information, even though the client didn’t use it.
Why Current Security Solutions Can’t Detect This
When we look carefully at the exploitation flow, we find the attack involved a very subtle change in the API call, replacing one user ID with another. In order to detect such a small change in the traffic, a deep understanding of the business logic of the app is required.
Current security solutions in the market lack that understanding, usually acting on the context of a single HTTP request. They don’t deeply understand important components of the application that are required to detect BOLA and other authorization vulnerabilities.
How Traceable AI Solves the Problem
The Traceable Defense AI approach to detect API attacks is very different than other security solutions. In a nutshell, it observes the data as it is passes through the API and the microservices of the app. It then uses machine learning algorithms to discover the application’s business logic, providing full visibility into the users and their roles, the API endpoints they communicate with, and the resources that the endpoints interact with behind the scenes.
This methodology allows Traceable to create a baseline of what a legitimate user’s flow looks like, and hence to detect the most sophisticated and subtle API attacks, including BOLA.
Interested to learn more?
Watch our recorded demo and see Traceable Defense AI in action!
The Inside Trace
Subscribe for expert insights on application security.
.avif)

