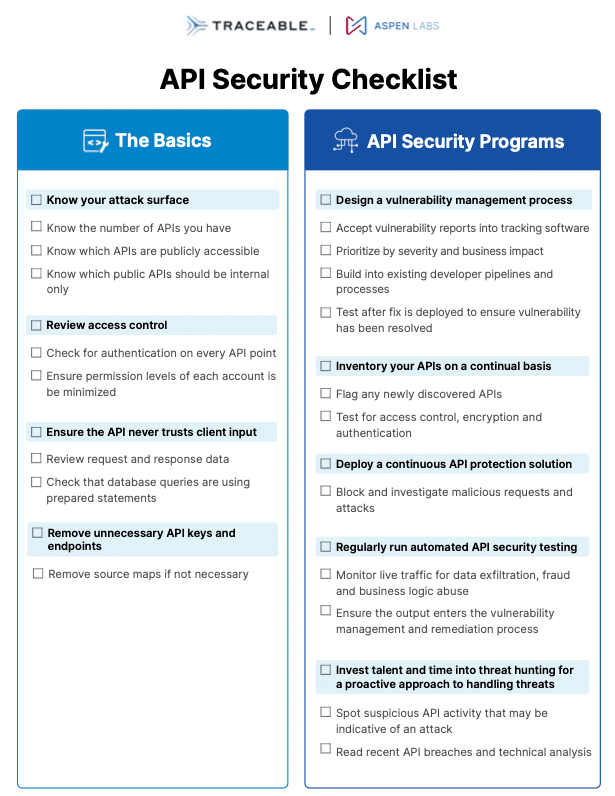
Featured Resources
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
No Results Found

Webinar
Start Your API Security Journey: Accelerate Secure Innovation with Traceable + AWS
Watch the replay of our AWS + Traceable webinar to discover key strategies for securing APIs in the cloud while maintaining speed and innovation.
Watch Now

Ebooks
View All Ebooks

Webinars
View All Webinars

Analyst Report
View All Analyst Report

Solution Brief
View All Solution Brief

Datasheet
View All Datasheet

Whitepapers
View All Whitepapers

.avif)