Application security from modern API security threats
Actionable insight into your current web application security and API security posture, effectively seeing into the ‘DNA’ of your application and associated APIs.
Traceable is continuously learning about how data flows into and within your applications. Enabling you to understand the real-time state of your application security, microservice security, and API security to detect and prevent attacks.
Application protection from traditional and emerging threats
Detect and block OWASP Top 10 and OWASP API Top 10 attacks. Machine learning continuously adapts to a changing threat environment, increasing your cloud-native security, confidence and reducing false positives.
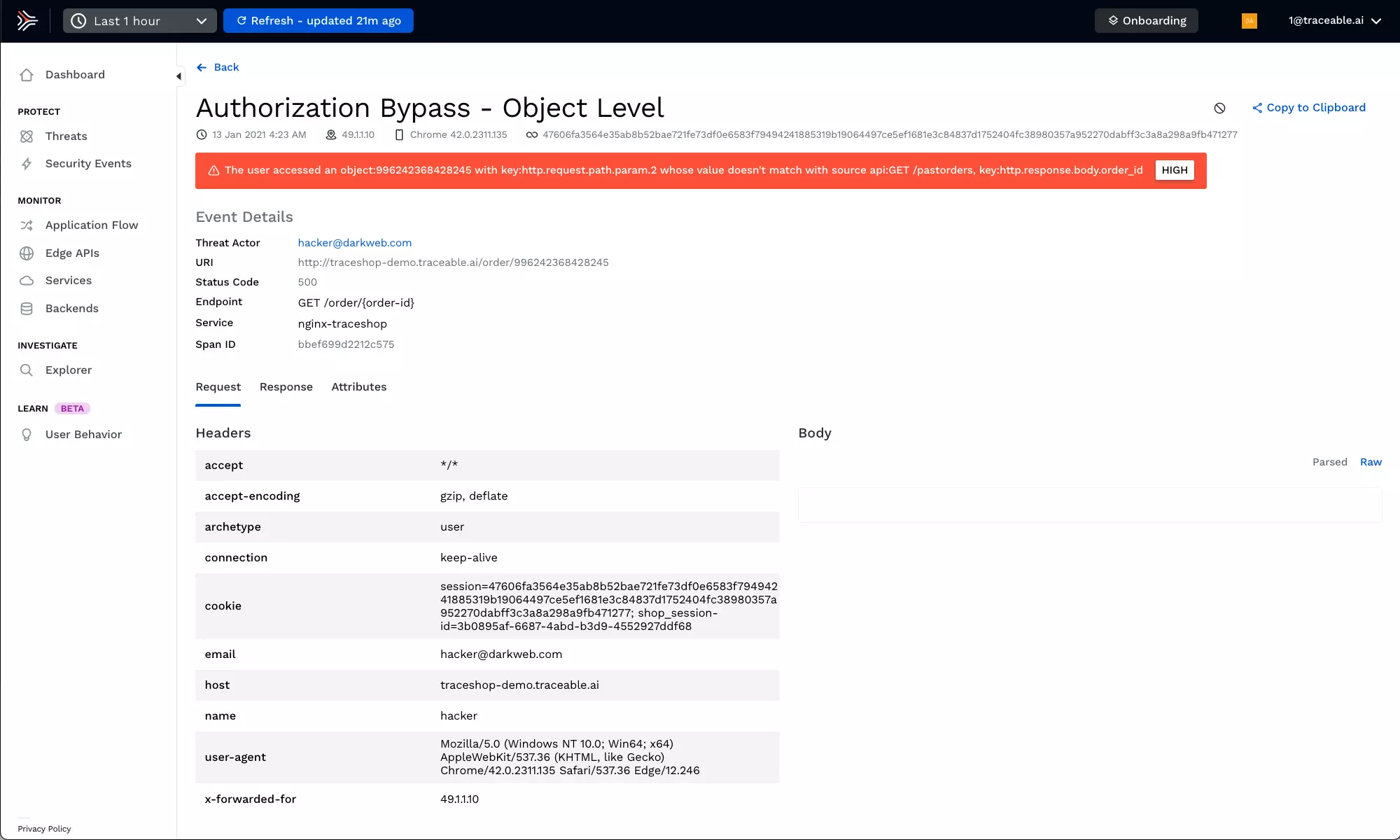
Microservices security from business logic attacks
Understand the flow of transactions through your application from edge to data and back to detect anomalies and quickly respond.
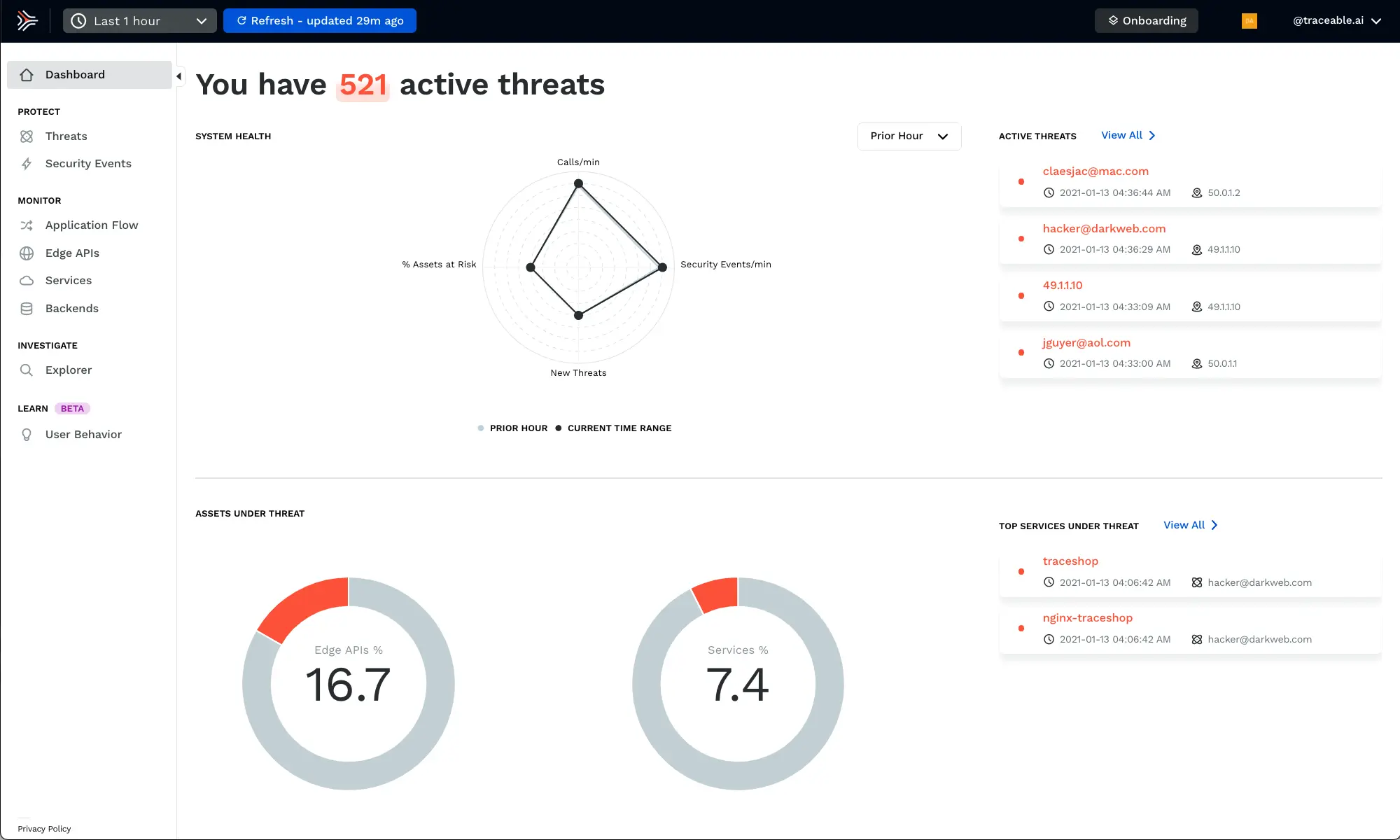
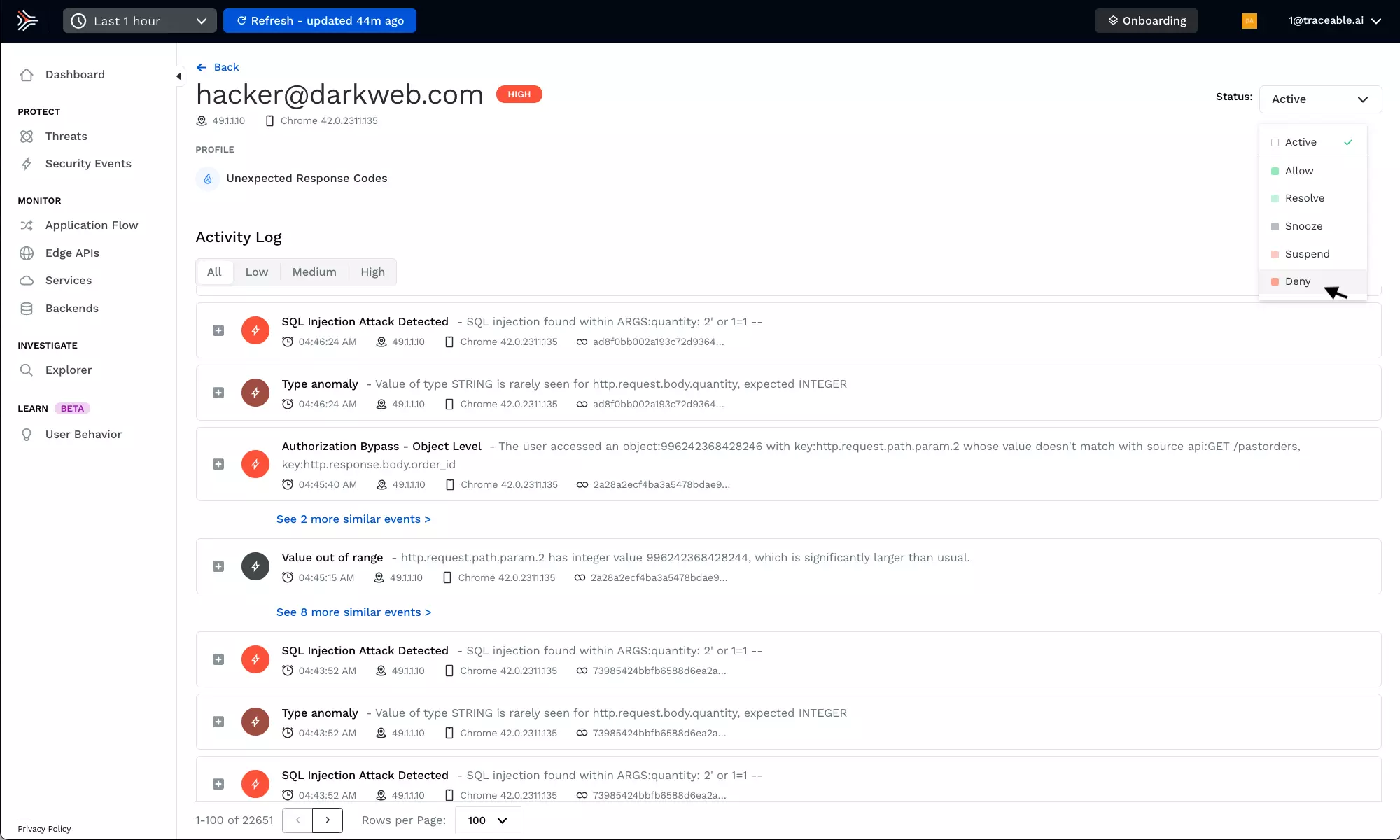
Continually identify and block threats
Continually track and correlate activities of threat actors across time, systems, and APIs to provide cloud-native security. Optionally block threats, often while they are in their reconnaissance stage.
Resources
11 Reasons Your WAF Can’t Secure Your APIs
WAFs are designed to protect your web applications from web application attacks. But they leave you vulnerable to API attacks. This blog discusses the 11 things that WAFs don’t do that are needed to properly protect APIs.
Key Takeaways from Forrester’s 2023 State of Application Security Report
Explore the key insights from Forrester’s State of Application Security report 2023 in our latest blog post. We delve into the complexities of application security, the rise of Software Composition Analysis (SCA), and the importance of API security in today’s digital landscape. Learn about the Shift-Everywhere movement and how it’s shaping the future of application security. This comprehensive analysis is a must-read for anyone looking to understand the current trends and challenges in application security.
Recent MOVEit Exploits: SQL Injection to Web Shell to Data Exfiltration
In the last few weeks, the security community has been shaken by a series of exploits targeting MOVEit, a popular file transfer software. These incidents have exposed critical vulnerabilities, allowing threat actors to compromise sensitive data and exploit organizations ranging from the BBS to several arms of the US Government.